update
|
Before Width: | Height: | Size: 125 KiB After Width: | Height: | Size: 125 KiB |
|
Before Width: | Height: | Size: 131 KiB After Width: | Height: | Size: 148 KiB |
|
Before Width: | Height: | Size: 132 KiB After Width: | Height: | Size: 151 KiB |
|
Before Width: | Height: | Size: 203 KiB After Width: | Height: | Size: 203 KiB |
|
Before Width: | Height: | Size: 133 KiB After Width: | Height: | Size: 133 KiB |
|
Before Width: | Height: | Size: 149 KiB After Width: | Height: | Size: 149 KiB |
|
Before Width: | Height: | Size: 185 KiB After Width: | Height: | Size: 185 KiB |
|
Before Width: | Height: | Size: 194 KiB After Width: | Height: | Size: 194 KiB |
|
Before Width: | Height: | Size: 99 KiB After Width: | Height: | Size: 131 KiB |
@@ -6,119 +6,119 @@
|
||||
|
||||
#### Slide 1
|
||||
|
||||

|
||||

|
||||
|
||||
Hey everyone, thanks for joining us here at this Meshtastic Workshop at Bitcoin 2024! My name is Adam Malin. By day I am a graphic designer at Oak Ridge National Laboratory, and by night I am a Bitcoiner trying to find the best freedom technology for me and my family.
|
||||
|
||||
I believe Bitcoin is crucial for preserving my time and energy. Nostr is crucial for securing my free speech.
|
||||
I believe Bitcoin is crucial for preserving my time and energy. Nostr is crucial for securing my freedom of speech online.
|
||||
|
||||
But what if internet and cellular networks go down? How will I communicate with my family or those I care about? This is where Meshtastic comes in.
|
||||
But happens when we have another Cloud Strike event, and critical internet and cellular services go down? How would you communicate with friends and family? This is where Meshtastic comes in.
|
||||
|
||||
Meshtastic and LoRa create a low-cost, low-power mesh relay network of long-range, encrypted radio devices. This network doesn't need cellular signal or WiFi to send text messages. The more people using Meshtastic and LoRa, the better the network coverage for everyone.
|
||||
Meshtastic and LoRa together can create a mesh relay network of encrypted radio devices. Because this network is its own infrastructure, it doesn't need cellular or WiFi signal to send text messages. The more people using Meshtastic and LoRa, the better the network coverage for everyone. Another way to think about this is to imagine LoRa is the Interstate System and Meshtastic is the car.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 2
|
||||
|
||||

|
||||

|
||||
|
||||
Before we keep going, there are two key points to cover:
|
||||
|
||||
LoRa is a cost-effective, low-powered mesh radio network designed for text data transmission over long distances without relying on cellular or WiFi signals.
|
||||
|
||||
Meshtastic combines radio firmware with an open-source app to enable communication over the LoRa mesh. This allows for seamless and encrypted communication across the network.
|
||||
Here are some of the topics we will try to cover today.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 3
|
||||
|
||||

|
||||

|
||||
|
||||
Always remember to attach your devices antenna before powering on a LoRa device to prevent damage. This is a crucial step for proper device functioning and to prevent damage to the radio.
|
||||
Before we keep going, there are two key terms to cover: LoRa and Meshtastic.
|
||||
|
||||
LoRa is a cost-effective, low-powered mesh radio network designed for text data transmission over long distances without relying on cellular or WiFi signals.
|
||||
|
||||
Meshtastic combines open-source radio firmware that is loaded onto these LoRa devices with an open-source app to enable communication over the LoRa mesh network. This allows for seamless and encrypted communication across the network.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 4
|
||||
|
||||
|
||||
|
||||
|
||||
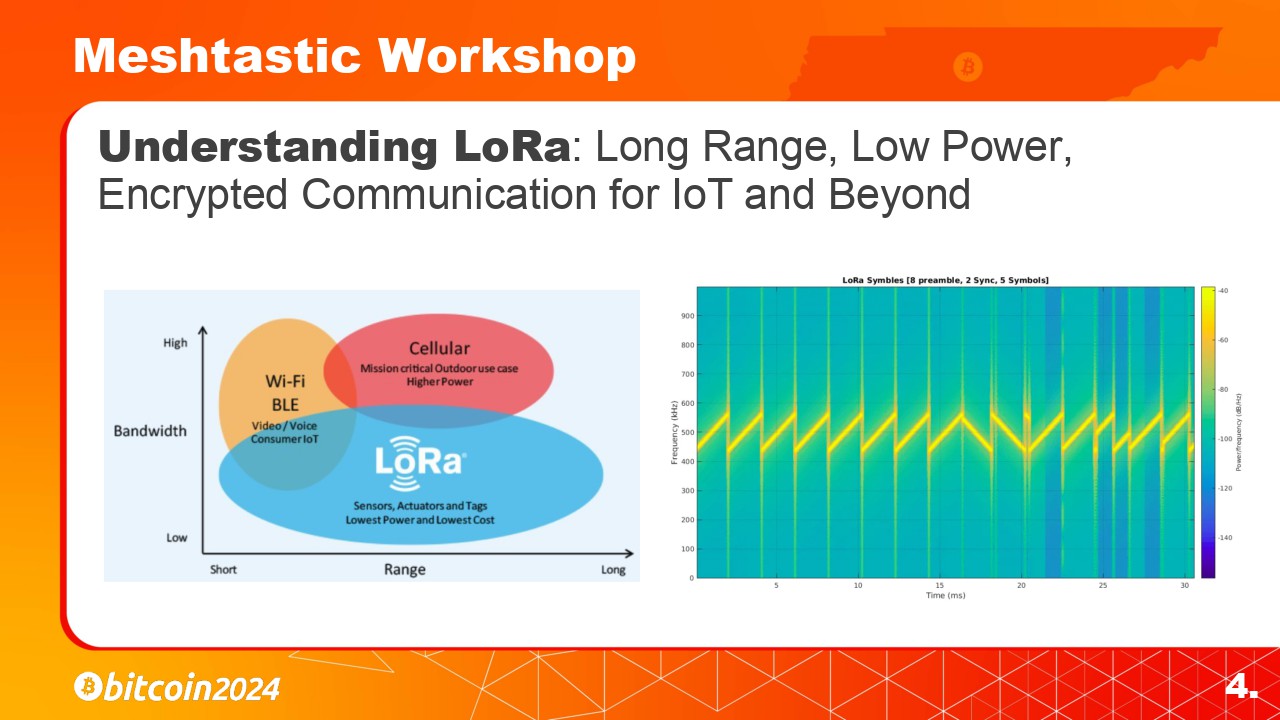
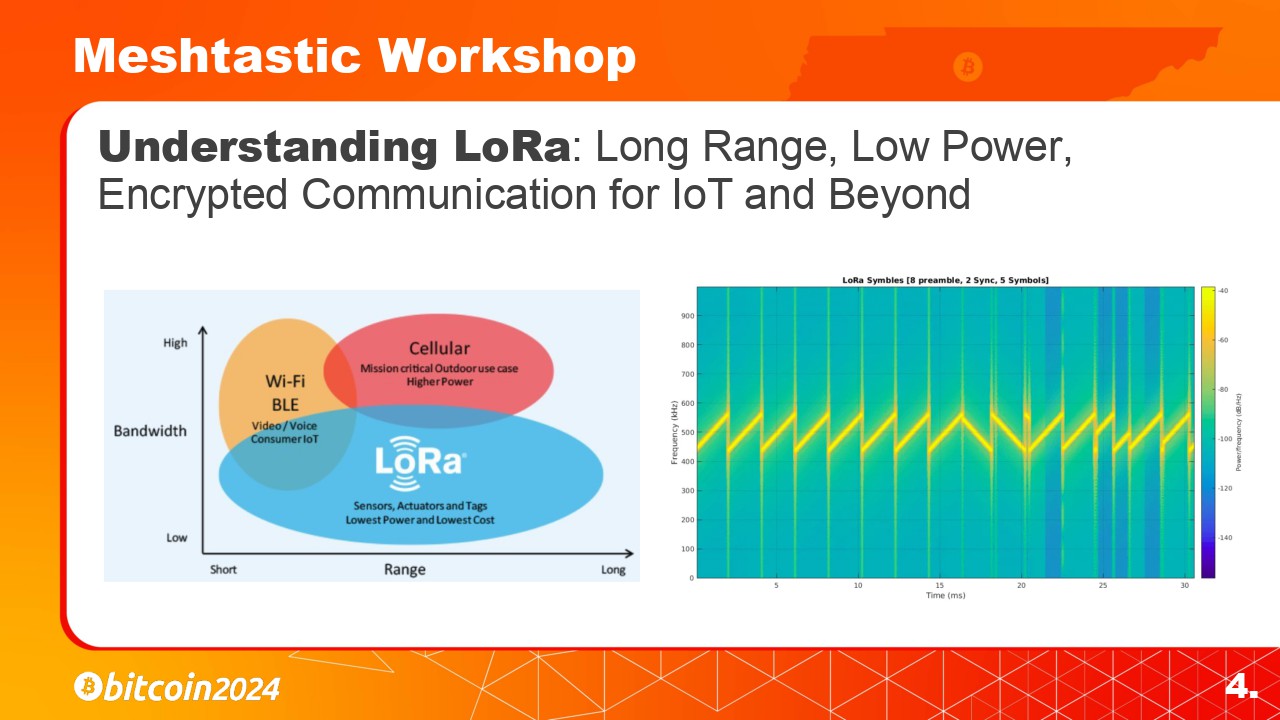
LoRa, which stands for Long Range, is a spectrum modulation technique derived from chirp technology. It operates on unlicensed frequency bands like 868 MHz in Europe and 915 MHz in North America.
|
||||
LoRa, which stands for Long Range, is a spectrum modulation technique. It operates on unlicensed frequencies like 868 MHz in Europe and 915 MHz in North America.
|
||||
|
||||
LoRa uses this ‘chirp pattern’ signaling method, which makes the signal robust, allowing it to penetrate through obstacles and cover long distances. Due to its low power consumption, LoRa devices can operate on batteries for weeks, making them ideal for remote or mobile deployments.
|
||||
LoRa uses a ‘chirp pattern’ signaling method, which allows the signal to better penetrate through obstacles and also cover long distances. Due to its low power consumption, LoRa devices can operate on batteries for weeks at a time, making them ideal for remote or mobile deployments.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 5
|
||||
|
||||

|
||||

|
||||
|
||||
LoRa is extensively used in IoT applications such as smart cities, agriculture, and environmental monitoring. Typically sending sensor data to and from remote locations. Its ability to transmit encrypted data over long distances with minimal power makes it ideal for these uses.
|
||||
LoRa has been extensively used in Internet of Things (IoT) applications such as smart cities, agriculture, and environmental monitoring. Typically sending sensor data to and from remote locations. LoRa’s ability to transmit encrypted data over long distances with minimal power makes it ideal for these situations.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 6
|
||||
|
||||

|
||||
Why Choose LoRa Over Ham Radio’s APRS for Secure Communication?
|
||||

|
||||
|
||||
Why did Meshtastic choose LoRa Over Ham Radio’s APRS for Secure Communication?
|
||||
|
||||
Ham radios are limited by FCC regulations on frequencies and power levels, and encoded messages are prohibited. This means that while Ham radio can be useful for many forms of communication, it falls short when it comes to securely transmitting encrypted data.
|
||||
|
||||
LoRa, on the other hand, provides an alternative options for encrypted communication. This is particularly important the potential of sending secure eCash transactions in the future. LoRa's ability to transmit encrypted messages over long distances with minimal power consumption makes it an ideal choice for secure and reliable communications.
|
||||
LoRa, on the other hand, provides an alternative options for encrypted communication. This is particularly important for the potential of sending secure eCash transactions in the future. LoRa's ability to transmit encrypted messages over long distances while using minimal power makes it an ideal choice for secure and reliable communications.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 7
|
||||
|
||||

|
||||

|
||||
|
||||
Meshtastic is an innovative, open-source chat application that leverages the LoRa Mesh for communication. It offers robust off-grid messaging capabilities, making it a powerful tool for truly decentralized communication.
|
||||
So now that we have discussed LoRa, lets move on to Meshtastic.
|
||||
|
||||
It’s important to understand that Meshtastic consists of two key components. Firstly, it is an app on your phone that you use to compose and send messages. Secondly, it includes custom firmware that is loaded onto a LoRa-capable radio. These two components work together seamlessly over Bluetooth. Your phone sends the message via Bluetooth to the LoRa radio, which then broadcasts the message to the local area over radio frequencies.
|
||||
Meshtastic is an innovative, open-source chat application that leverages the LoRa Mesh for communication. It enables off-grid messaging capabilities, making it a powerful tool for a truly decentralized communication network.
|
||||
|
||||
It’s important to understand that Meshtastic consists of two key components. Firstly, it is an app on your phone that you use to write and send messages. Secondly, it includes custom firmware that is loaded onto a LoRa-capable radio. These two components work together seamlessly over Bluetooth. Your phone sends the message via Bluetooth to the LoRa radio, which then broadcasts the message to the local area over the radio frequencies.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 8
|
||||
|
||||

|
||||

|
||||
|
||||
To get started with Meshtastic, the first step is to select a suitable LoRa and Meshtastic capable device based on your needs. Examples include Heltec v3, T-Beam, T-Deck, or Wizblock. There are many more.
|
||||
How do you get started with Meshtastic? The first step is to select a suitable LoRa and Meshtastic capable device based on your needs. Examples might include Heltecs, T-Beams, T-Decks, or Wizblocks and many more.
|
||||
|
||||
It’s crucial to choose the correct LoRa frequency for your region. For instance, the U.S. uses LoRa 915 MHz, while other regions might use 868 MHz or other frequencies. Ensure you have the right hardware for your location to achieve optimal performance.
|
||||
It’s crucial to choose the correct LoRa frequency for your region. For instance, the U.S. uses LoRa 915 MHz, while other regions might use 868 MHz or other frequencies. Ensure that you have the right hardware for your location.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 9
|
||||
|
||||

|
||||

|
||||
|
||||
Because these devices are such low power, there are many ways you can choose to power them.
|
||||
Next we will talk about setting up a Meshtastic device. Because these devices are such low power, there are many ways you can choose to power them.
|
||||
|
||||
1. Laptop/USB
|
||||
2. Small Solar Panel
|
||||
3. A Coinkite ColdPower
|
||||
4. A USB battery bank
|
||||
From Laptops and USB ports to solar panels, battery banks and even Bitcoin hardware like a ColdPower could be used.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 10
|
||||
|
||||

|
||||

|
||||
|
||||
Once you have selected the right device and power method, next we will need to flash the Meshtastic firmware.
|
||||
Once you have selected the right device and power method, next we will need to flash the Meshtastic firmware onto the radio.
|
||||
|
||||
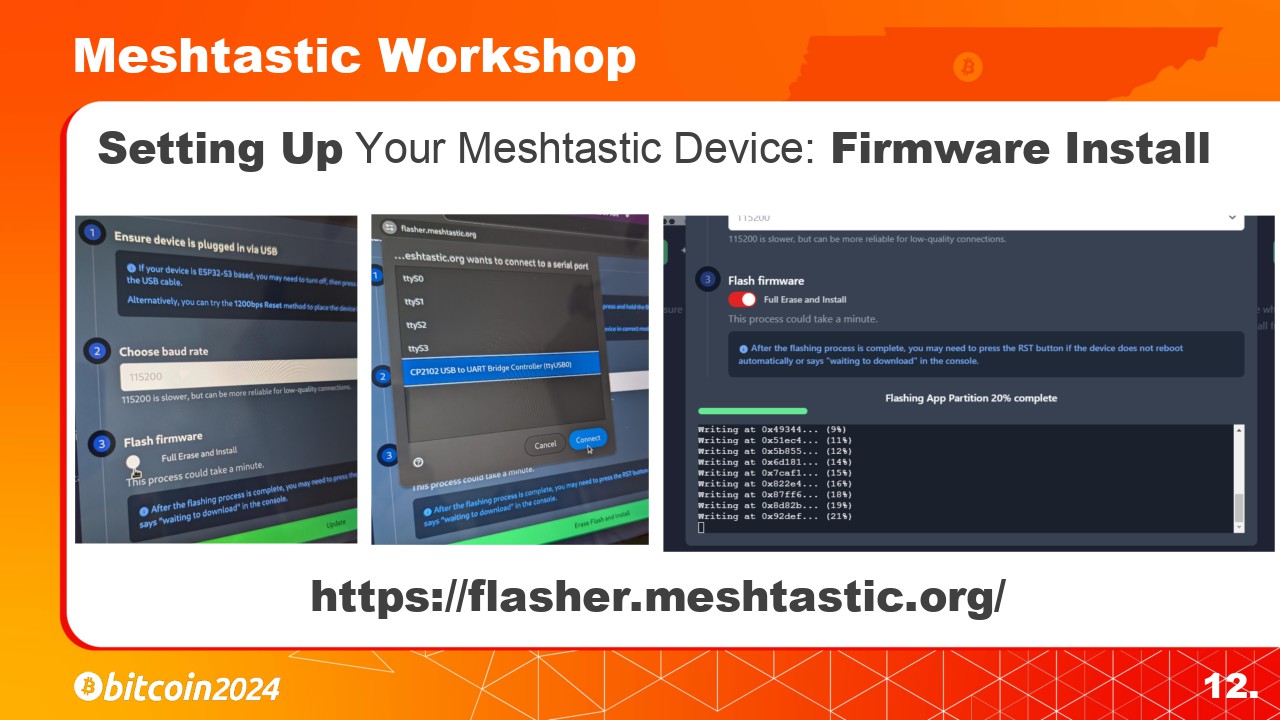
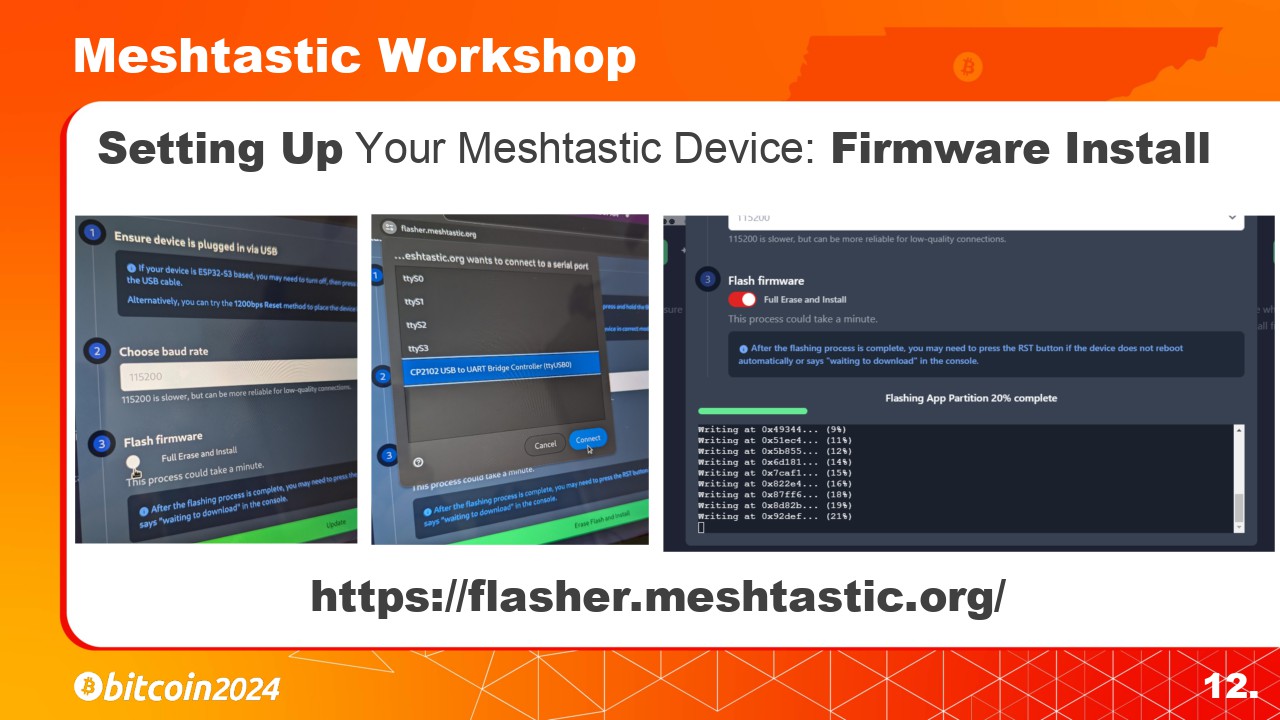
In this example we will be using the HelTec V3. Make sure to connect your antenna before powering one the radio. Once connected to your computer you should see a screen that looks like this on the LoRa device.
|
||||
In this example we will be using the HelTec V3. Make sure to connect your antenna before powering one the radio. Once connected to your computer you should see a screen that looks like this on the LoRa device.
|
||||
|
||||
To flash your device with the correct firmware we will be using the Meshtastic online device flashing tool and the Chrome web browser.
|
||||
To flash your device with the correct firmware we will be using the Meshtastic online device flashing tool and the Chrome web browser.
|
||||
|
||||
Something to note here: If your using a Linux distribution and your Chrome browser is a containerized application like an AppImage or flatpak format you might have connection issues between the browser and the LoRa device. So try using an integrated version of Chrome via APT or another integrated package manager. At the moment this process does usually go more smoothly on a Windows PC.
|
||||
Something to note here, If your using a Linux distribution and your Chrome browser is a containerized application like an AppImage or flatpak format you might have connection issues between the browser and the LoRa device. So try using an integrated version of Chrome via APT or another integrated package manager. At the moment this process does usually go more smoothly on a Windows PC.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 11
|
||||
|
||||

|
||||

|
||||
|
||||
Go to flasher.meshtastic.org and select the correct device that you have connected using the first drop down menu.
|
||||
Once connected, go to flasher.meshtastic.org and select the correct device that you have connected using the first drop down menu on the left.
|
||||
|
||||
Then select the version of the firmware you with to install. I typically use the latest Stable version.
|
||||
|
||||
@@ -128,9 +128,9 @@ And then select the Flash button on the right.
|
||||
|
||||
#### Slide 12
|
||||
|
||||
|
||||
|
||||
|
||||
You will then be asked if you wish to Erase and Install the new firmware. We want to select Yes.
|
||||
You will then be asked if you wish to “Erase and Install” the new firmware. We want to select Yes.
|
||||
|
||||
Then the Chrome browser will ask for permission to connect to the device. If you are unsure which USB device it is then you can just unplug the LoRa device and plug it back in to see which one pops up again. Click “Connect” then click the “Erase Flash and Install” button.
|
||||
|
||||
@@ -138,17 +138,17 @@ Then the Chrome browser will ask for permission to connect to the device. If you
|
||||
|
||||
#### Slide 13
|
||||
|
||||

|
||||

|
||||
|
||||
Now were done on the LoRa device side of things. You should now see a Meshtastic screen on the device with a connection code under the logo. We will use this to connect our phone with this radio.
|
||||
Now were done on the LoRa device side of things. You should now see a Meshtastic screen on the device with a connection code under the logo. We will use this one-time code to connect the phone to this radio.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 14
|
||||
|
||||
|
||||
|
||||
|
||||
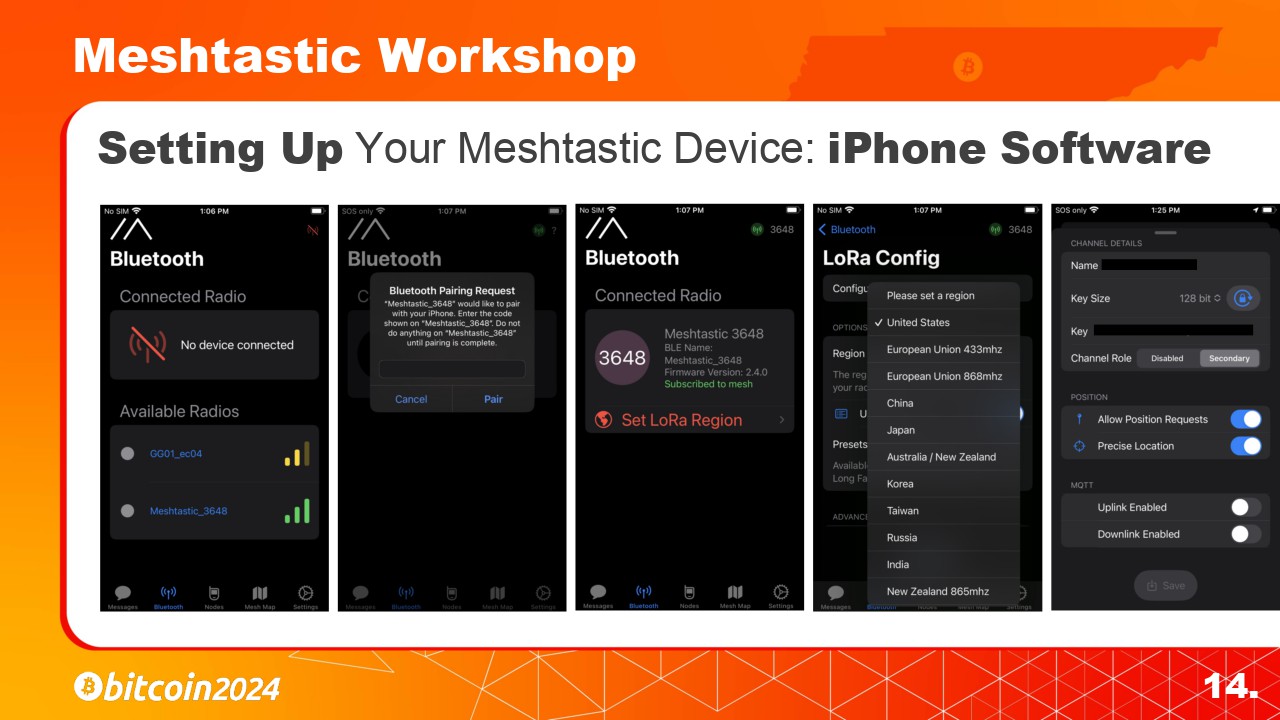
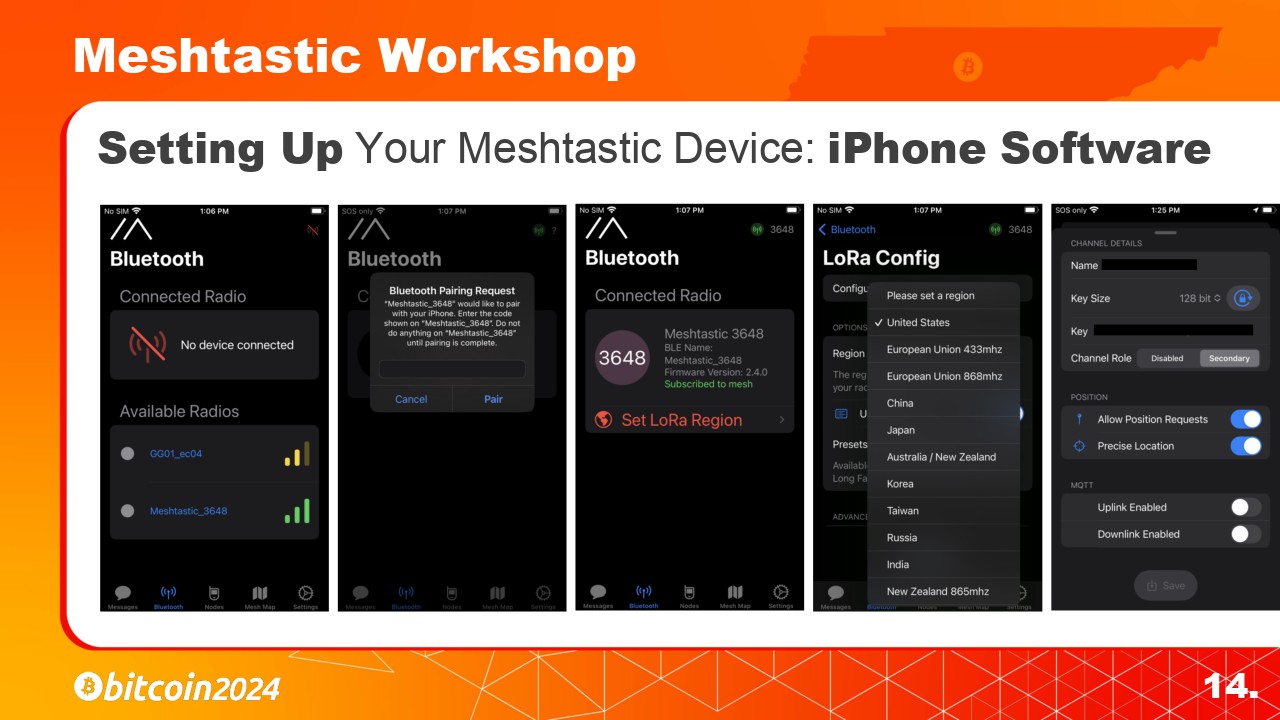
To connect your phone to your Meshtastic enabled radio we need to install the Meshtastic app on your Android or iPhone.
|
||||
To connect your phone to your Meshtastic enabled radio we need to install the Meshtastic app on your Android or iPhone.
|
||||
|
||||
I’ll will start with the iPhone version of the app.
|
||||
|
||||
@@ -156,94 +156,89 @@ I’ll will start with the iPhone version of the app.
|
||||
|
||||
2. Set the LoRa Region to “United States”.
|
||||
|
||||
3. Then you can setup the public and private channels. The default public channel is called “LongFast”. Its key is AQ== and is known to everyone.
|
||||
|
||||
I will show how to easily connect to our Bitcoin Conference Channels later in the slides. And this presentation will be available for download.
|
||||
3. Then you can setup the public and private channels. The default public channel is called “LongFast”. Its encryption key is AQ==. This key is known to everyone.
|
||||
|
||||
Later in the slides I will show how to connect to the Bitcoin Conference Channels we have setup. Also this presentation will be available to download for reference.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 15
|
||||
|
||||
|
||||
|
||||
|
||||
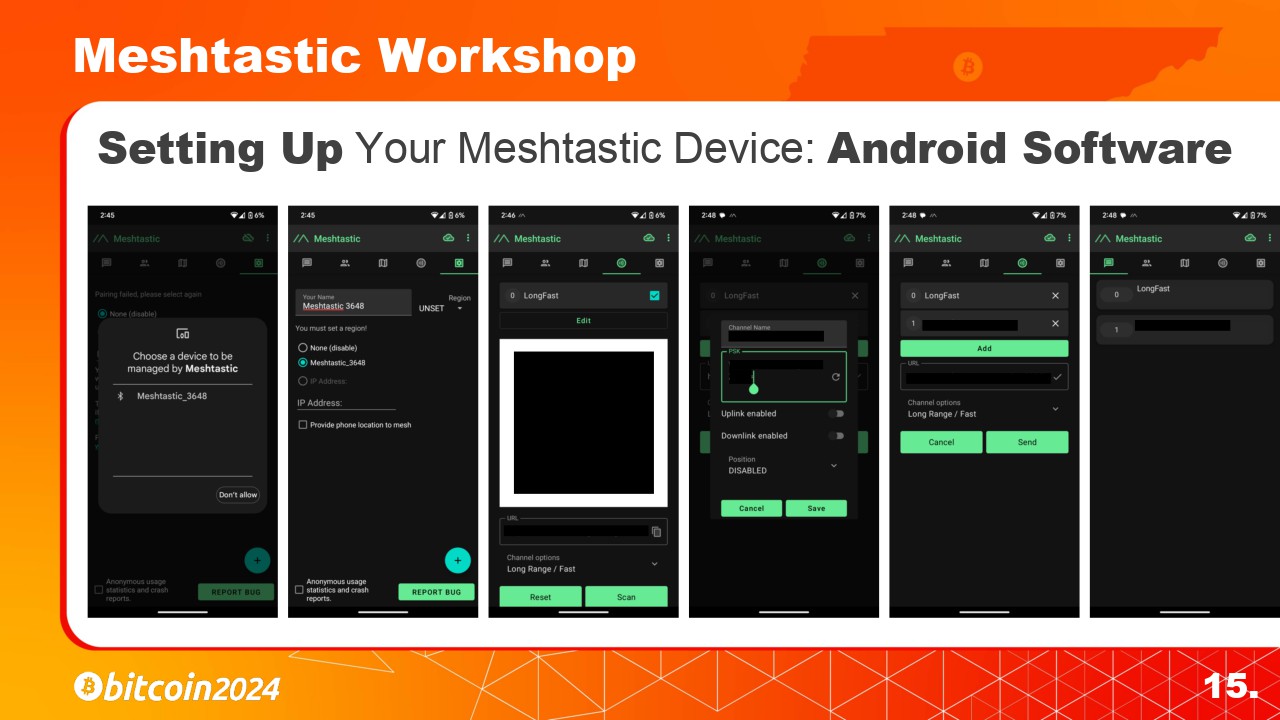
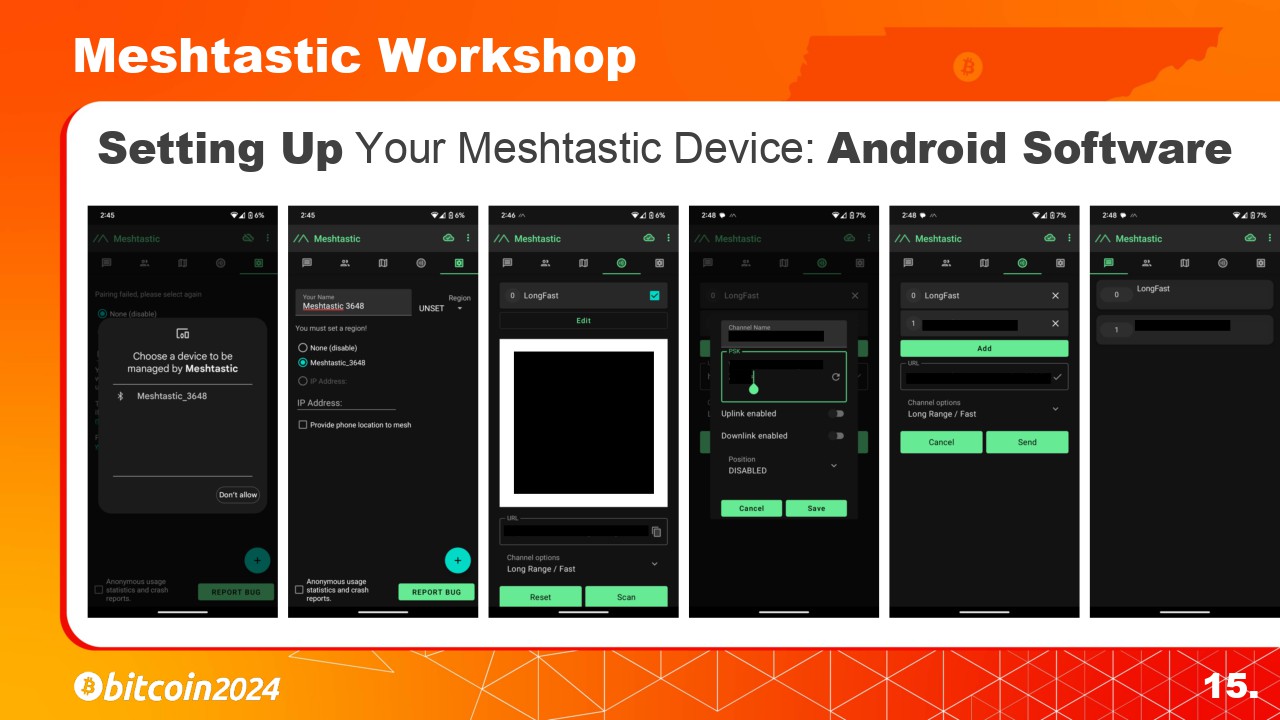
Next lets walk through the Android setup since they are slightly different.
|
||||
Next lets walk through the Android setup since they are slightly different.
|
||||
|
||||
1. With the Meshtastic Device powered on, Click the + button to add the nearby Meshtastic Device using the code on the LoRa devices screen.
|
||||
1. After installing the Meshtastic App, power on the device and then Click the + button to add the nearby device. Then put in the one-time code from the LoRa devices screen.
|
||||
|
||||
2. Change the Region to “US”.
|
||||
|
||||
3. Select the “Channel” tab and click on “Edit” to add your own private channels here.
|
||||
|
||||
4. Click on “Add Channel” and enter the Channel Details or Scan the QR code and have it set automatically. If you already have channels setup be sure to save the URL or QR code for restoration later before scanning the new QR code.
|
||||
4. Click on “Add Channel” and enter the Channel Details or Scan the QR code and have it set automatically. If you already have channels setup be sure to save the URL or QR code for restoration later before scanning this new QR code.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 16
|
||||
|
||||

|
||||

|
||||
|
||||
If you already have a Meshtastic Device, you can join our private Bitcoin Conference chat channels. Here is the information you will need to connect. Open the Meshtastic app, go to the Channels tab and scan the code.
|
||||
If you already have a Meshtastic Device, you can join our private Bitcoin Conference chat channels that we have setup. Here is the information you will need to connect. Open the Meshtastic app, go to the Channels tab and scan the code.
|
||||
|
||||
Again, If you already have some custom channels setup make sure to backup your configuration or save your Channel URL somewhere so you can restore them later before scanning this code.
|
||||
Again, If you already have some custom channels setup make sure to backup your configuration or save your Channel URL somewhere so you can restore them later before scanning this code.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 17
|
||||
|
||||

|
||||

|
||||
|
||||
Ok, now we will take a deeper look at how Meshtastic works over LoRa to create a reliable communication network. The Meshtastic mesh broadcast algorithm includes four conceptual layers:
|
||||
Ok, now we will take a deeper look at how Meshtastic works over LoRa to create a reliable communication network. The mesh broadcast algorithm includes four conceptual layers:
|
||||
|
||||
Layer 0: LoRa radio as the base of the network.
|
||||
The base layer is the LoRa Radio. On top of that we have “Unreliable Zero Hop Messaging” then “Reliable Zero Hop Messaging” and finally on the top we have “Naive Flood Routing” for multi-hop messaging.
|
||||
|
||||
Layer 1: Unreliable Zero Hop Messaging
|
||||
|
||||
Layer 2: Reliable Zero Hop Messaging
|
||||
|
||||
Layer 3: Naive Flooding for Multi-Hop Messaging
|
||||
|
||||
Each layer is crucial for ensuring reliable and efficient communication over the mesh network.
|
||||
Each layer is crucial for ensuring reliable and efficient communication over this network.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 18
|
||||
|
||||

|
||||

|
||||
|
||||
Layer 0 is the LoRa Radio, which handles the conversion of data into the chirp LoRa symbols. This layer forms the foundation of Meshtastic communication.
|
||||
Layer 0 is the LoRa Radio. This handles the conversion of data into the chirp LoRa symbols. This layer forms the foundation of all Meshtastic communication.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 19
|
||||
|
||||
|
||||
|
||||
|
||||
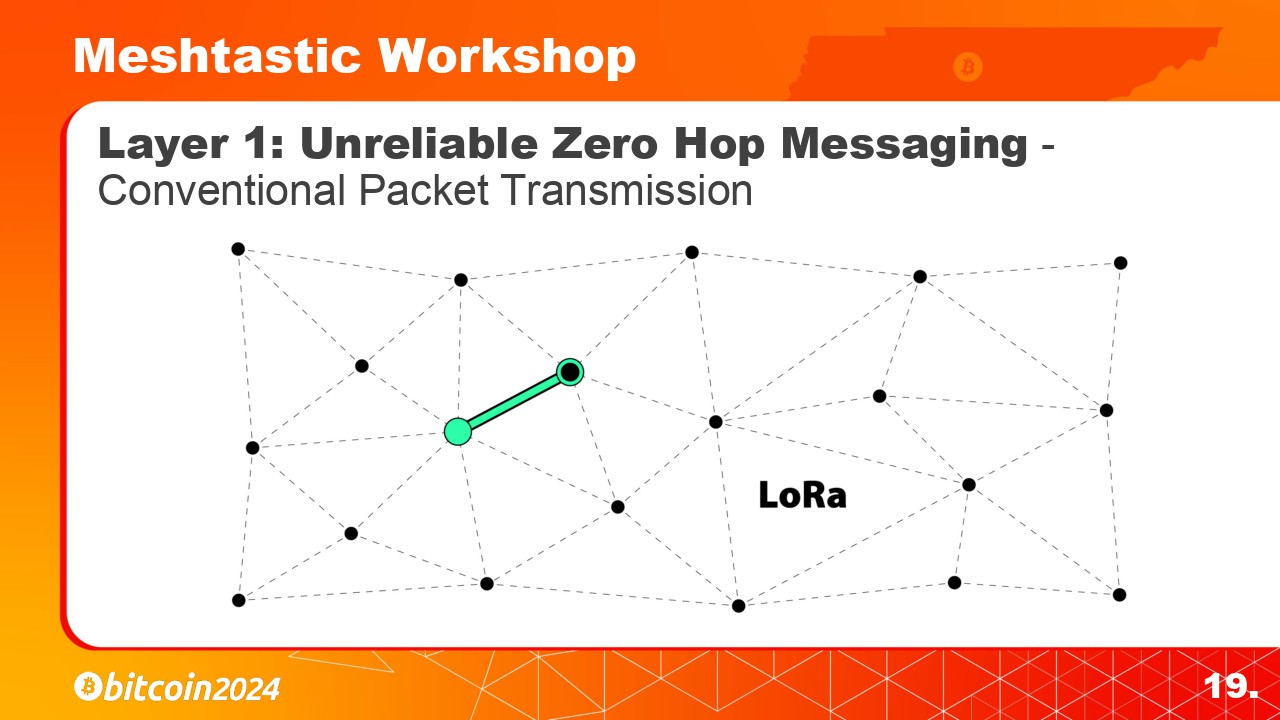
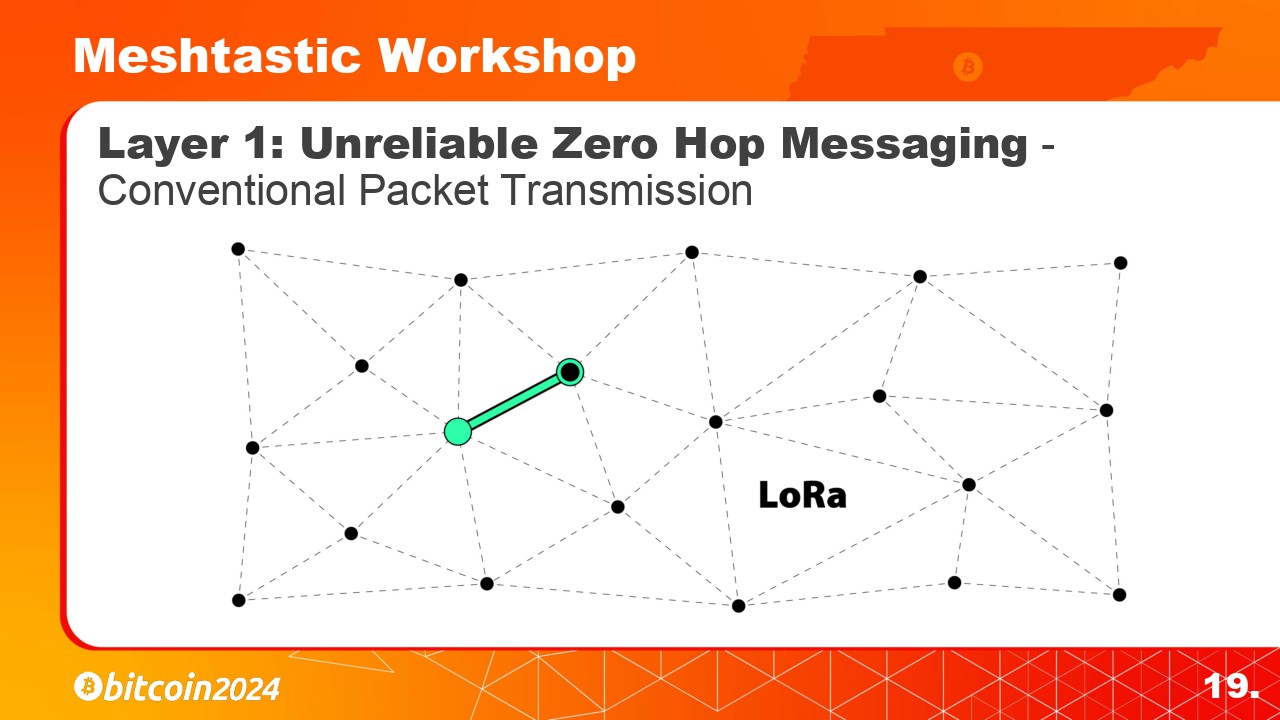
Layer 1 handles Unreliable Zero Hop Messaging, which includes conventional LoRa packet transmission from one node to another. Packets are equipped with identification data, followed by encrypted payload data. Nodes perform checks at this stage before transmitting to avoid signal collisions.
|
||||
Layer 1 handles Unreliable Zero Hop Messaging. This includes conventional LoRa packet transmission from one node to another. These packets are equipped with identification data, followed by encrypted payload data. At this stage, the nodes perform checks before transmitting to avoid signal collisions.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 20
|
||||
|
||||

|
||||

|
||||
|
||||
Layer 2 adds reliability to the messaging process by sending what is called a “WantAck” flag. This is a request for the receiver to acknowledge delivery of the message from the sender. Broadcasting Nodes listen for these acknowledgments or “ACKs”. If no “ACK” is received, then the packet is retransmitted up to three times to ensure delivery.
|
||||
Layer 2 adds reliability to the messaging process by sending what is called a “WantAck” flag. This is a request for the receiver to acknowledge delivery of the message from the sender. Broadcasting nodes listen for these acknowledgments or “ACKs”. If no “ACK” is received, then the packet is retransmitted up to three times to ensure successful delivery.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 21
|
||||
#### Slide 21
|
||||
|
||||
|
||||
|
||||
|
||||
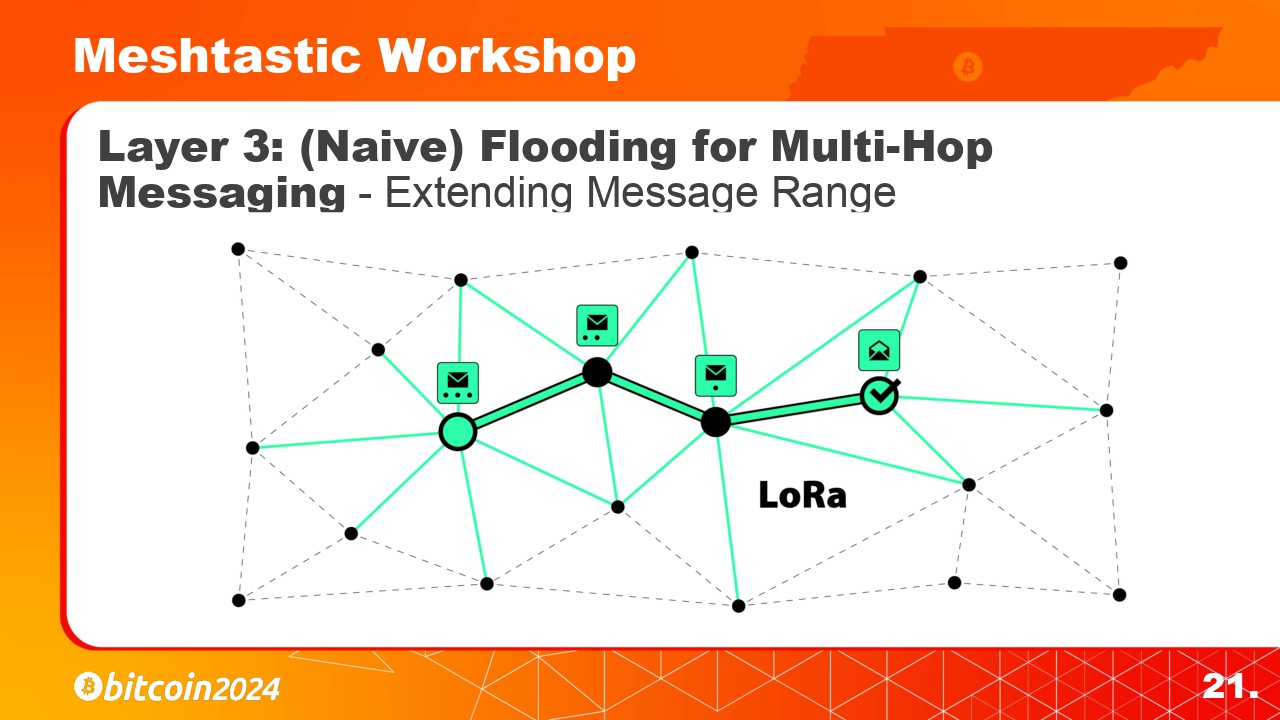
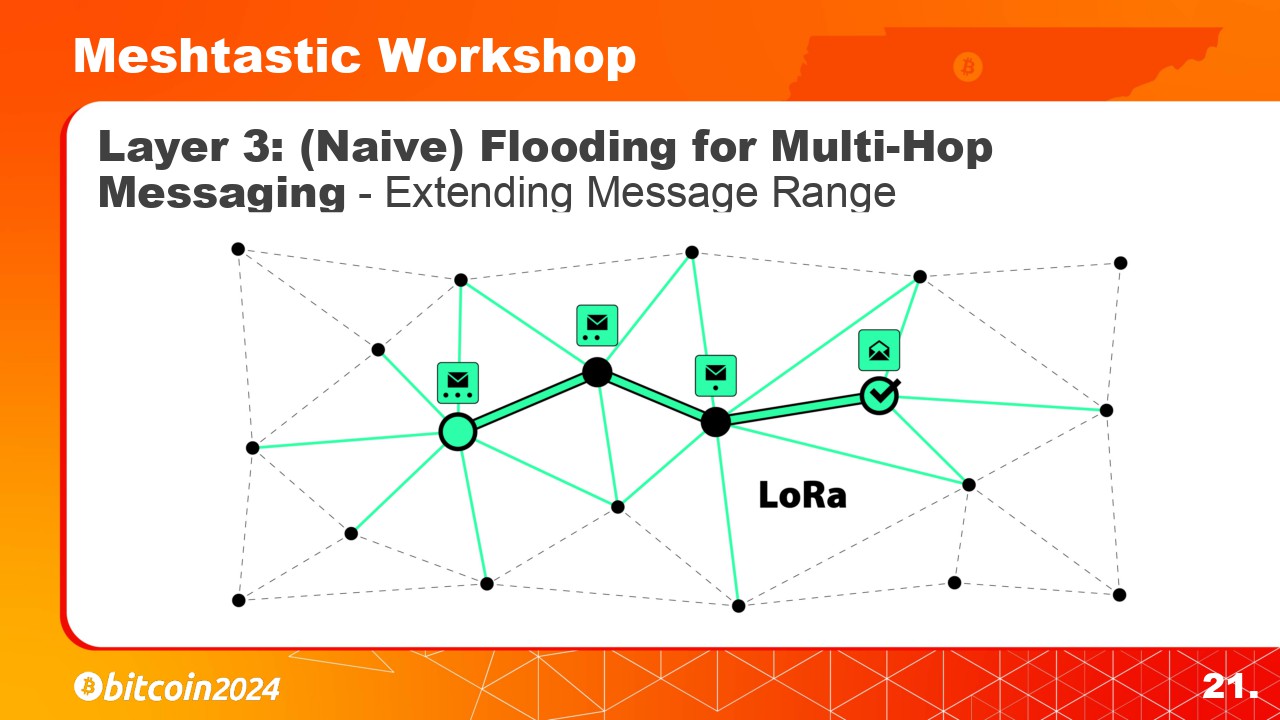
Layer 3 uses flooding to propagate messages across the network. Nodes reduce the HopLimit and retransmit the message if needed. Nodes further away with lower Signal-to-Noise Ratio (SNR) rebroadcast first to extend the message range.
|
||||
Layer 3 uses flood routing to propagate messages across the network. Nodes reduce the HopLimit and retransmit the message they received if needed. Nodes further away with lower Signal-to-Noise Ratio (SNR) rebroadcast first to extend the message range.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 22
|
||||
|
||||

|
||||

|
||||
|
||||
For optimal performance, Meshtastic devices, also known as nodes, should be placed in locations with a clear line of sight to each other. Obstructions such as hills and buildings can reduce the range of these nodes and increase the need for more nodes in the area to maintain reliable communications.
|
||||
Now that we understand how Meshtastic works, lets look at how we can optimize this network for sending our messages.
|
||||
|
||||
Devices, also known as “nodes”, should be placed in locations with a clear line of sight to each other. Obstructions such as hills and buildings can reduce the range of these nodes and increase the need for more nodes in the area to maintain reliable communications.
|
||||
|
||||
A “node” in this context refers to any device in the network that can send, receive, or relay messages.
|
||||
|
||||
@@ -251,39 +246,31 @@ A “node” in this context refers to any device in the network that can send,
|
||||
|
||||
#### Slide 23
|
||||
|
||||
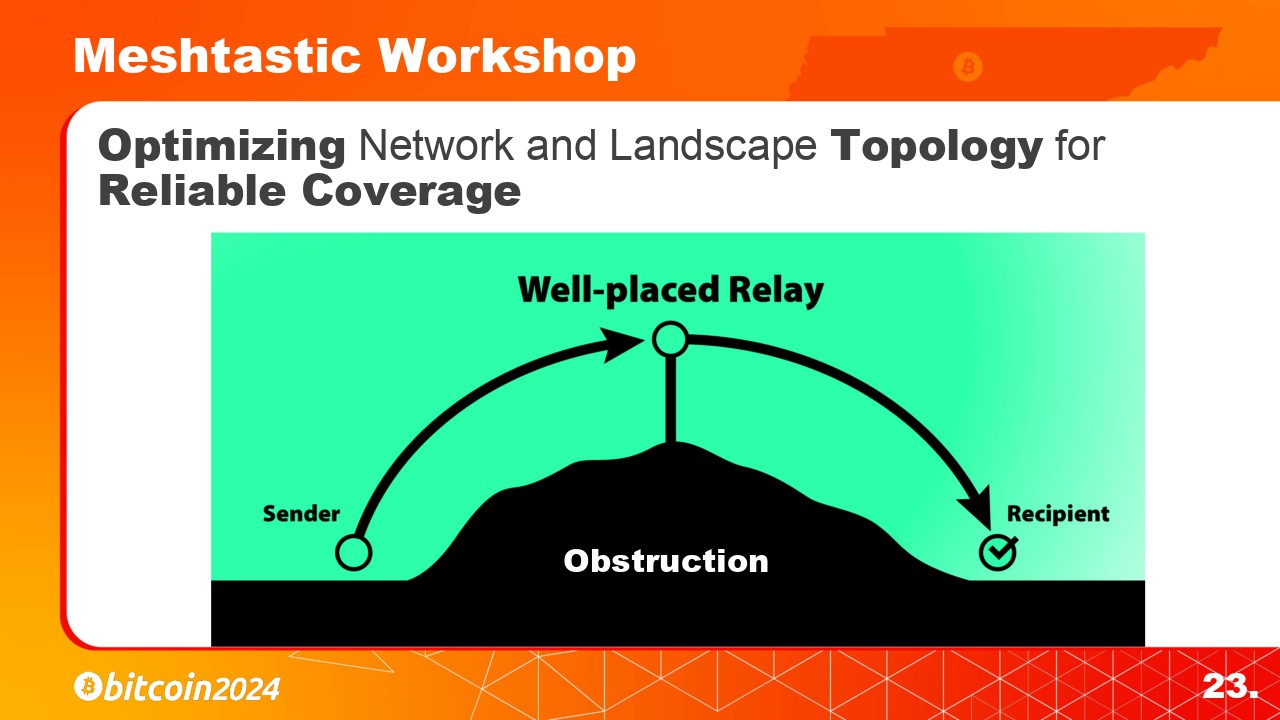
|
||||
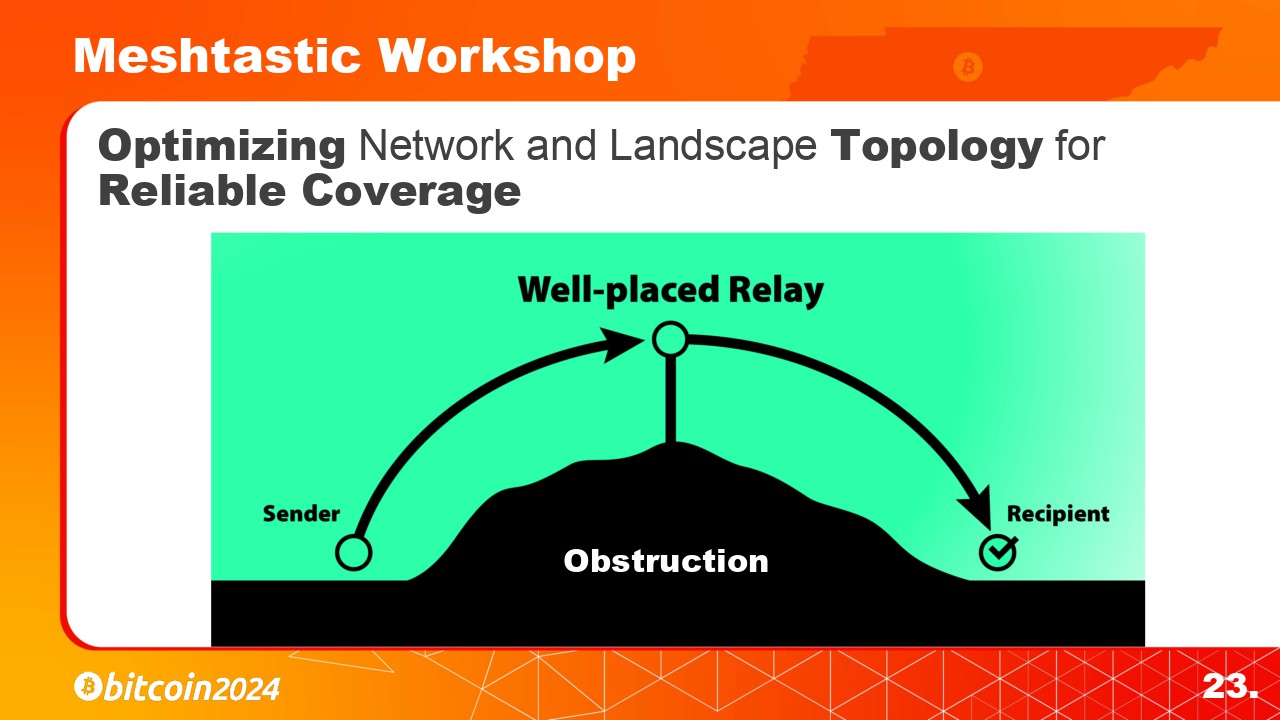
|
||||
|
||||
Here is an example of a well placed node at the top of this hill. This node is able to relay the messages and expand the networks reach.
|
||||
Here is an example of a well placed node at the top of this hill. This node is able to relay the messages and expand the networks reach.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 24
|
||||
|
||||

|
||||

|
||||
|
||||
Let's talk about Meshtastic and encryption one more time. Here we will look at how keep communications secure for yourself and those in your channels.
|
||||
Let's talk about how Meshtastic uses encryption so we can better understand how keep our messages secure.
|
||||
|
||||
Meshtastic uses strong AES256 encryption to secure your messages, ensuring they remain private.
|
||||
Meshtastic does use strong AES256 encryption to secure its channels, ensuring that messages sent within these channels remain private.
|
||||
|
||||
Each channel has its own unique key. By default, there’s a simple key everyone knows which is AQ== for the default LongFast channel. For better security on our Bitcoin Conference Channels, we set up the channels with a unique key and have shared it with everyone here outside the mesh.
|
||||
Each channel in has a unique key used for encryption. This key is used to encrypt messages sent within that channel, including direct messages between users on the same channel. The default LongFast channel has a publicly known key (AQ==). This means that anyone can join this default channel, and messages sent over this channel are not secure since the key is publicly available. For better security, it is recommended to create private channels with unique keys. These keys should be shared securely (using a secure communication method like Signal) with those you want to communicate with. This ensures that only intended participants can access the channel.
|
||||
|
||||
Direct Messages over Meshtastic are not as secure as using a dedicated shared and private channel since the encryption key for the DMs is known to everyone of your contact is from the default LongFast Channel. Its best for security to send Channel Keys to new users you would like to communicate with outside the mesh network and not through DMs.
|
||||
|
||||
Let's look at some other important security considerations when using Meshtastic.
|
||||
|
||||
Always keep your radio device secure. If someone gets access to your device, they could potentially access your communications, since the Channel Key is stored on the LoRa radio device.
|
||||
|
||||
Be careful with sharing your channel QR code or URL with others. Only share it with trusted people to keep your messages and the messages of others in your channels private.
|
||||
|
||||
Remember, encryption can be turned off if needed like for “Ham Radio mode”, but it's best to keep it on for privacy.
|
||||
Direct messages in Meshtastic are not as secure if the initial contact was made on the default LongFast channel because the encryption key for DMs would be the same publicly known key. Therefore, it is better to use private channels with unique keys for more secure communications. Sharing the channel keys outside the mesh network and not through DMs on the default channel adds an extra layer of security.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 25
|
||||
|
||||

|
||||

|
||||
|
||||
Here are some practical use cases for Meshtastic and LoRa, showing how these technologies can be effectively utilized in various scenarios.
|
||||
Next we will look at when you might use Meshtastic. Here are some practical examples showing how these technologies can be effectively utilized in various scenarios.
|
||||
|
||||
Rural Area Connectivity: LoRa/Meshtastic can provide reliable communication in rural areas where traditional infrastructure is lacking or nonexistent.
|
||||
|
||||
@@ -295,23 +282,23 @@ Disaster Response: During natural disasters or other emergency situations, when
|
||||
|
||||
#### Slide 26
|
||||
|
||||

|
||||

|
||||
|
||||
I want to also shout out ‘The Comms Channel’ (TC2) on YouTube. He has some of the most informative and comprehensive Meshtastic content available. He’s working on some really cool Meshtastic related projects, like his Meshtastic BBS server as well as various Solar Meshtastic node designs. So, if you're interested in building out your area with Meshtastic nodes, whether that be for solar, mobile, or a home base stations, check out his content. I’m sure you will find it helpful.
|
||||
That wraps up my content. I want to also shout out ‘The Comms Channel’ (TC2) on YouTube. He has some of the most informative and comprehensive Meshtastic content available. He’s working on some really cool Meshtastic related projects, like his new BBS server as well as various Solar node designs. So, if you're interested in building out your area with nodes, whether that be for solar, mobile, or a home base stations, check out his content. I’m sure you will find it helpful.
|
||||
|
||||
---
|
||||
|
||||
#### Slide 27
|
||||
|
||||

|
||||

|
||||
|
||||
Feel free to reach out to me on Nostr at thePR0M3TH3AN if you have any other questions that we don't cover today!
|
||||
Feel free to reach out to me on Nostr at thePR0M3TH3AN if you have any other questions that I don't cover today!
|
||||
|
||||
---
|
||||
|
||||
#### Slide 28
|
||||
|
||||

|
||||

|
||||
|
||||
Before we move into the Q&A segment, let’s recap the key takeaways from today’s workshop:
|
||||
|
||||
@@ -329,10 +316,10 @@ Now, I’d be happy to answer any questions you may have.
|
||||
|
||||
#### Slide 29
|
||||
|
||||

|
||||

|
||||
|
||||
Here are some links to Meshtastic resources as well as a download link for this entire presentation.
|
||||
|
||||
The large QR code here are the Bitcoin Conference Meshtastic Private Channels. Scan them and join in on the conversation over the radio waves.
|
||||
The large QR code is the Bitcoin Conference Private Channels. Scan to join in on the conversations.
|
||||
|
||||
Thanks for joining us for this Meshtastic workshop, I hope it was informative and enjoy the rest of the conference!
|
||||